
In Cyber Security, AAA is the framework used for managing user activity through:
- AUTHENTICATION: This is when you verify your credentials, like with a password or username, for example.
- AUTHORIZATION: This is what the user is allowed to access to while they’re logged in the network.
- ACCOUNTING: This is when you track the actions performed by a user while they were logged in to the network.
In these notes, we go over the authentication portion of AAA.
But first, here are some FAQ’s about the subject that I ended up researching to better understand it.
AAA vs AAAA
The Network+ exam objectives guide references AAAA (Authentication, Authorization, Accounting, Auditing) as an important acronym to memorize for the test.
While studying, or at least Google searching for AAAA, you probably came up with two kinds of results:
1. AAAA record (as in a “Quad-A record”)
2. AAA in Cyber Security

AAAA and AAA essentially falls under the Cyber Security subject. But Accounting and Auditing are two different things.
Accounting is when every action a user makes on a network is tracked and accounted for. This can be achieved through user logs, for example.
Auditing is the actual paper trail associated with the accounting. So for instance, let’s say an independent group comes to your job and asks to see user activity from 1:54 pm on October 12, 2021 through 7:49 pm on October 12, 2021. How would you present this information to the independent group?
That’s what they mean by auditing – you should be able to produce receipts for every action a user has made on your network.

WHATS THE POINT OF AUTHENTICATION AGAIN?
Hackers. Stolen data. Data protection and privacy is an ever changing subject because the people trying to steal the data are constantly evolving.
In the Incident Report podcast, I talked about what happened when employees of Sony Pictures had their user authentication credentials intercepted by hackers back in 2014.
It was a mess. To this day, the victims of the data breech still has their names, social security numbers, medical data, and other important info on the Dark Web. Even their kids were threatened with identity theft, and some of their information is still on the dark web, too.
I swear, every day hackers try new ways to steal data, and unfortunately there are more success stories than not. The best way to protect stolen data starts with the individual user. And as network engineers who will be policing those policies, it is up to you to know all about authenticating principles and techniques on a network.

AUTHENTICATION WITH A VPN CONCENTRATOR
In Professor Messer’s N10-007 lesson on AAA, he discussed what authentication would look like on a network. In that conversation, he mentioned a user logging on to a network, and then being stopped by a VPN Concentrator/Firewall in order to authenticate their credentials before gaining access to a company’s network.
What was that all about?
A VPN concentrator is a tool used in networking to allow remote users to access a company’s encrypted VPN tunnel to authenticate their credentials on a network.
For example, if you’ve ever worked from home, you probably had to log in to a VPN client portal of some sort to access the company’s network.
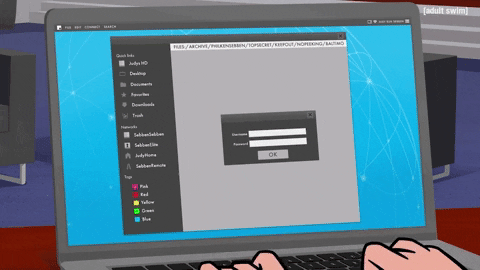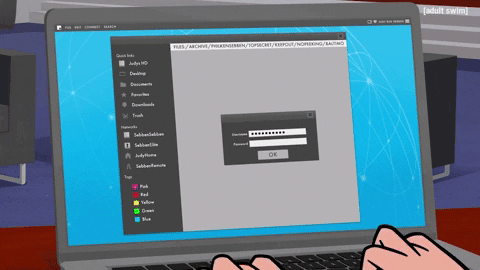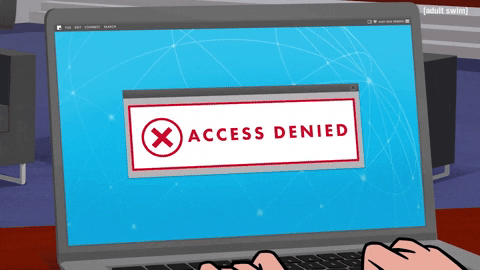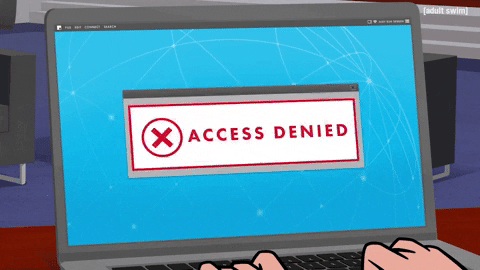
Or if you took classes online, had a doctor’s appointment, or even paid a bill online, you probably had to go somewhere over the internet to login.
Privacy Affairs has the best explanation on what a VPN concentrator is, and how it works.
VPN Concentrators use tunneling protocols to create and manage VPN tunnels. It receives incoming data, de-encapsulating and decrypting the data. It encapsulates the outgoing network data into encrypted packets and then transmits the data through the VPN tunnel.
A VPN Concentrator also manages user authentication and assigns users’ IP addresses. It also manages the cryptographic keys and handles network communications using standard VPN protocols.
In principle, VPN Concentrators act like a router but add an extra layer of security to the network traffic.
PrivacyAffairs.com
CLICK THE NEXT PAGE TO READ ABOUT AUTHENTICATION PROTOCOLS


